Threat Actors Leveraging AI driven Third Party Applications for Business Email Compromises
During the course of a business email compromise (BEC) investigation in an M365 environment, IDX identified the malicious use of a third-party application called Attio.
It is not uncommon for threat actors to install third party applications in M365 to synchronize and download emails. In fact, IDX blogged previously about the use of PerfectData Software which can synchronize and download a user’s entire mailbox.
What makes Attio interesting in the context of a BEC case is that it is an AI driven content relationship manager (CRM) solution, aimed more at marketing and sales teams rather than a traditional data exfiltration tool. Attio documentation supports this as well, stating that emails cannot be exported (https://attio.com/help/referen...).
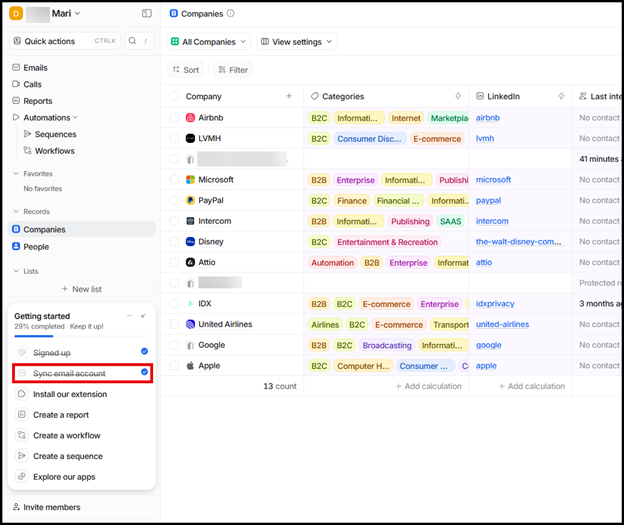
So why would threat actors want to leverage this application? One reason may be that Attio displays companies that the user interacts with, and the strength of that relationship. The screenshot below, taken from the Attio website, demonstrates this functionality. Each company the user has interacted with via email is listed, along with the connection strength:
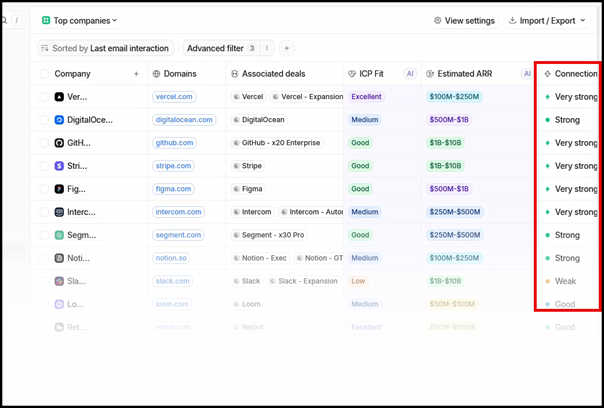
A threat actor can leverage this intelligence to identify high-value targets for wire fraud or launch phishing campaigns from the compromised account. If that user has a strong relationship with a company, it can increase the likelihood of a successful phishing link being clicked from a known contact.
Attio Installation
Attio is a web-based customer relationship management (CRM) application and requires a business email to create an account. When creating an account or signing into Attio, a one-time passcode (OTP) is sent from attio.com to the associated email account, and that must be used to sign in. This means to access Attio, the threat actor must maintain access to the compromised account so they can receive the code to login.
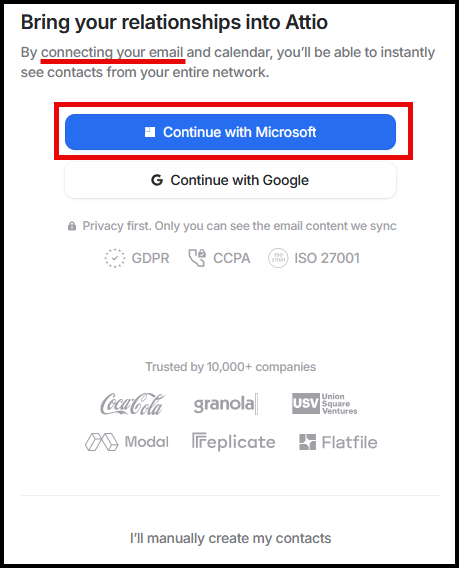
Once logged in, the user is presented with the option to link their M365 account. To do so, they must authenticate with their M365 account:
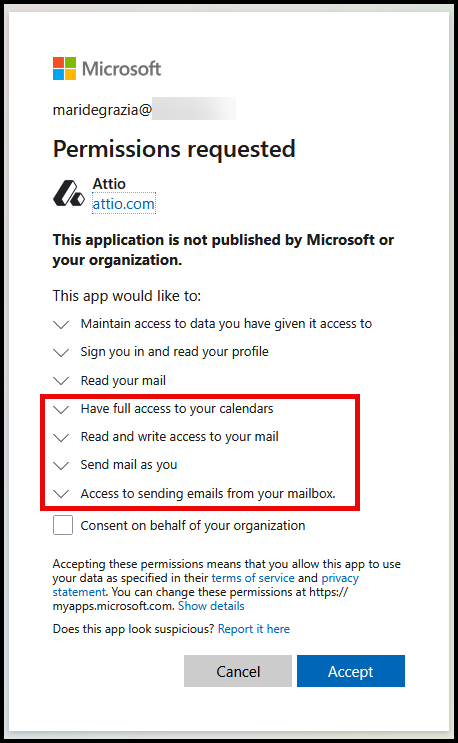
If the user decides to link their account, they grant the following permissions to the Attio application:
By default, users are allowed to register third party applications in M356. This is a setting IDX recommends turning off.
Once the user completes these steps, they have a dashboard like the below, with an indication that their email has been synched.
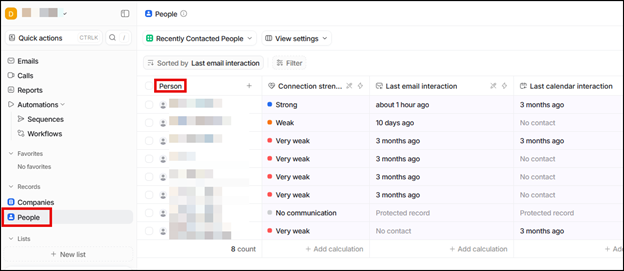
At this point in time, the threat actor can interact with and view emails. However, the process is a bit arduous for reviewing emails vs a traditional email application such as Outlook. For example, to view emails, you click People, select a person, then view emails from that person.
Locating Indicators of Compromise
There are several ways to check to see if Attio has been installed within the M365 environment. This can help establish when the application was installed as well as any associated user accounts.
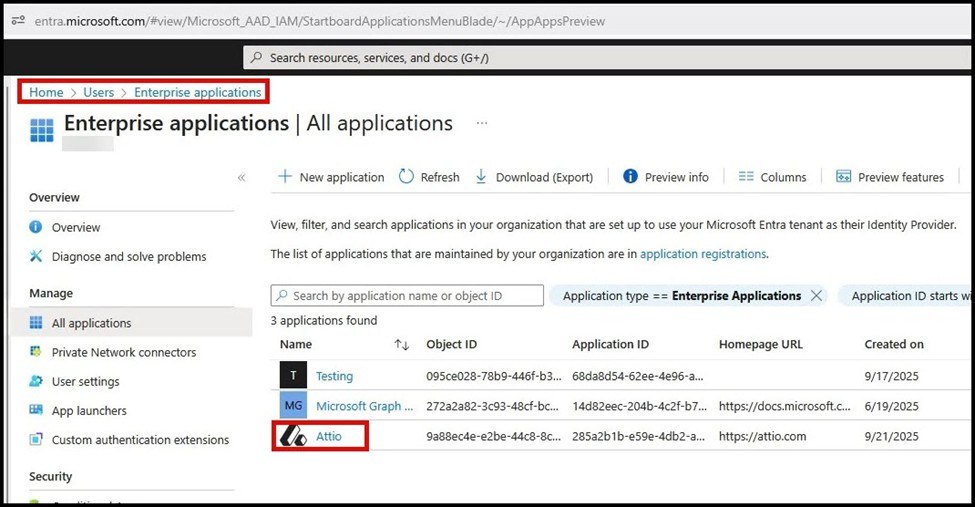
Check for unknown or suspicious installed applications to include Attio in Microsoft Entra under Home > Users> Enterprise applications:
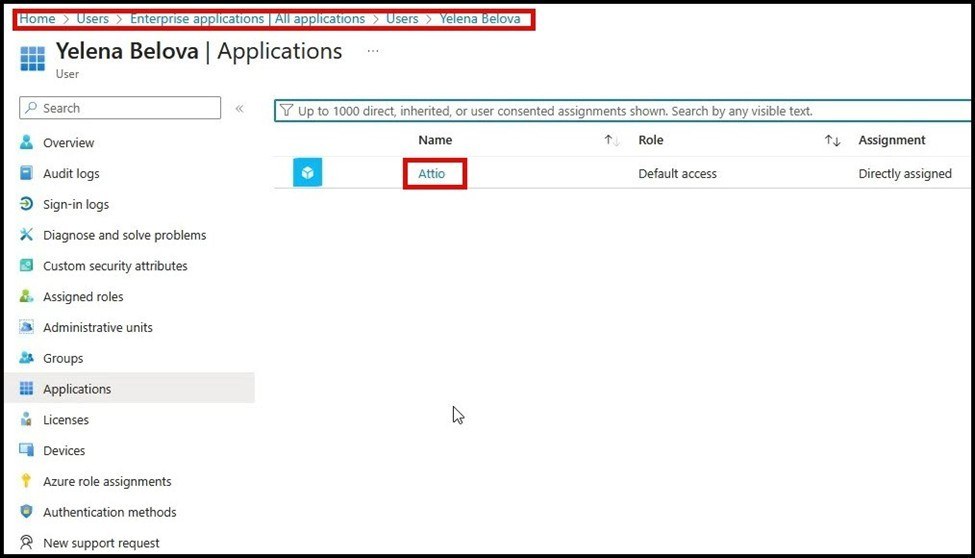
Check compromised users for recently installed applications, to include Attio, under Users > Enterprise applications > All applications > Users:
Attio sends several emails throughout the process as well as each time it sends a code for the user to sign in. You can search for the following in the M365 environment or message trace logs:
“Welcome to Attio!”
“Your Attio Temporary Password”
“Your email has finished syncing with Attio”
“Your Attio trial has ended”
“Your email has stopped syncing with Attio”
Attio has the application ID 285a2b1b-e59e-4db2-a862-e0d06751e637. Search the Unified Audit Logs for this application ID to find related activity.
You can also check the Unified Audit Log for the “Add app to role assignment grant to user”, “Consent to application” and “Add service principal” with references to “Attio” in the audit data.
Mail Items Accessed
When Attio syncs, it will create a Mail Items Accessed record in the Unified Audit log for each email that has synced with the Attio application, however, this does not necessarily mean that the emails were viewed.
IDX Response Recommendations
- Disable Unauthorized Apps: Do not delete unauthorized third-party apps identified in your tenant. Deleting the application reduces the amount of information you may be able to identify that will help in an investigation.
- Thorough Investigation: Conduct a thorough investigation into potential email compromises.
- Revoke Permissions: Revoke any OAuth tokens or permissions granted to unauthorized apps.
- Block App Reinstallation: Block the app's client ID to prevent its reinstallation.
- Limit User Consent: Configure Microsoft 365 to limit or disable users from being able to install third-party applications.
- Admin Approval for Apps: Require admin approval for any new application installations to ensure proper vetting before granting access.
- Regular Reviews: Regularly review and audit applications and permissions granted within your Microsoft 365 environment.
- User Training: Educate users on the risks associated with granting permissions to third-party applications, allowed applications for the organization, and the importance of following proper approval processes.
- Implement Consent Policies: Implement app consent policies that allow user consent for apps from verified publishers with low-impact permissions.
About IDX
We're your proven partner in digital privacy protection with our evolving suite of privacy and identity products.
